The world is changing more rapidly than ever before. Organisations are facing an extremely complicated and unique set of conditions in the SAP security environment. Growing threats from the shift in hackers’ focus towards directly attacking SAP systems have been intensified by the huge rise in home working brought about by the COVID-19 pandemic. Businesses had to hastily enable distributed access to their key business systems, with little time to consider the security aspects.
On top of this, users are isolated from peers and supervisors, and have more freedom to explore the limits of their access, or download ‘interesting’ data. An example of this type of enhanced insider threat was recently reported at a global e-commerce platform (Shopify). This case emphasises that it has never been more important to ensure that users’ access is properly aligned with their actual job requirements, and to address vulnerabilities with RFC connections and associated security problems.
Added to this, organisations have to increase their clock speed to stay competitive and relevant. The time they take to get products to the market, to make organisational changes, to take up new projects and so on has had to be reduced enormously. This requires agile thinking, which started as a development concept, but moved to a mindset of how the organisation functions.
It’s estimated that today’s average large organisation requires a clock speed 3-5 times faster than the equivalent organisation a decade ago.
Dudley Cartwright, Soterion CEO
Increase in fraud and data theft risk
Increase in audit and compliance requirements
Increase in regulations such as Data Privacy Regulations
While the pandemic and increasing cyber threats are putting extra pressure on IT teams, the need for large transformation and S/4HANA projects cannot be slowed. These projects bring their own challenges with respect to security and Access Risk, including access via Fiori apps, the obligation to use Business Partners, and security at the database level.
The well-known audit principle of the three lines of defence relies on effective collaboration from:

First line: Business/Operational users
Second line: Risk and Compliance Departments
Third line: Audit and Assurance
It’s clear that relying on audit and risk departments to identify risk is not good enough. To get effective value from all three lines, the business needs to take ownership of their risk. However, most businesses are already thinly stretched; surely they don’t have the capacity to take on more work, or added responsibilities?
So, organisations need to look for a more effective way to manage their risk. Think in terms of this analogy: An army of foot soldiers versus a handful of tanks. Effective GRC is about empowering the business users to become foot soldiers. These foot soldiers have a good understanding of the terrain (risks). You will have business users with 15 to 20 years of experience who know the risks facing the organisation, and understand the processes that support it; and you need to use that experience to focus on the risks that have the most impact.
To relate it back to the analogy: If there was an army protecting their border, and this army has three divisions:
Division 1: Foot Soldiers who walk up and down the border wall looking for weaknesses or signs of intrusion. As with employees, there are many of them who know the terrain like the back of their hands.
Division 2: Lookout Towers who monitor the border. As with risk and compliance departments, they have great tools at their disposal, but their numbers are limited, and the towers are spaced five miles apart, resulting in sections where they have no visibility.
Division 3: Surveillance planes, who monitor the border from the air. As with audits, they are very effective, but due to the cost of keeping the planes in the air, they are used sporadically.
If this army had their foot soldiers patrolling the border, but the army generals felt it was not necessary to provide them with any communication devices, they would be ineffective. While patrolling, they would see weaknesses in the border or infiltration points, but they would be powerless to notify headquarters of these breaches.
If that same army provided communication devices to the foot soldiers, they would be able to call for backup when they spotted any suspicious activity. This would allow the surveillance plane to be deployed when it is most needed, and will be most effective.
The changing environment, and increased risk, has turned Access Risk into a business risk. The days of pushing it to a specialist team are in the past. The business needs to become accountable. However, most GRC tools don’t support this. Traditional GRC tools have been developed from a technical perspective – they have been good for auditors and admin users, but not for business or operational users. The latter find the tools too technical and not user-friendly, which leads to increased resistance and low adoption.
GRC activities can also be seen as ‘ticking an audit box’ activities, which don’t add much value to the organisation. When the mindset is changed to have a business-centric approach to GRC, this viewpoint changes, and organisations benefit from really owning and managing their Access Risk.
A good example of where a business took ownership of their risk is captured in a case study for Aker Solutions. They used Soterion to identify the risks in their system, and also to reduce them substantially.
Aker Solutions in Norway were not seeing the benefits expected from their SAP GRC solution. Soterion was implemented within one week, with tangible results being released even from the first day. Within six months, they were able to reduce Access Risk by 85%. Perhaps most importantly, they were able to get their business stakeholders involved, with their Senior Vice President Financial reporting and compliance commenting, “Finally we have a tool to give us insights and visibility in our roles and authorisations.”
Read more about their experienceTo solve the GRC challenges organisations are facing, Soterion Technologies developed a suite of solutions focusing on providing protection in an agile, business-centric way. This engagement is achieved via intuitive, easy-to-use dashboards and graphics, with drill-down ability; process flows that show where the risk lies in the business process; easy rule-set customisation and clean-up wizards, as well as comparison views across user groups and departments. Soterion’s approach caters for all SAP enterprise sizes and can be deployed rapidly into a client’s landscape, either on their own hardware or as a cloud-based service.
Once deployed, users can experience benefits immediately and Access Risks can be reduced in a short period of time. A prime focus of Soterion is to provide business-centric GRC, giving business users the tools to proactively manage and model risks within specific business departments. This allows them to take responsibility for the management of Access Risk in their area, freeing up the Security Administration and Compliance departments to focus on more strategic tasks. These business users, who know the business process intimately, can also be engaged to review the rule-set and customise it to reflect their company’s reality, which can be turned into an effective first line of defence for GRC.
Soterion is S/4HANA and Fiori ready and has rule-sets for other SAP systems, such as SRM and CRM. It can also detect SoD conflicts across different systems. It has an innovative Privacy rule-set, which helps to facilitate GDPR compliance by showing who has access to the PII of Employees, Vendors, Customers and Business Partners in the SAP system.
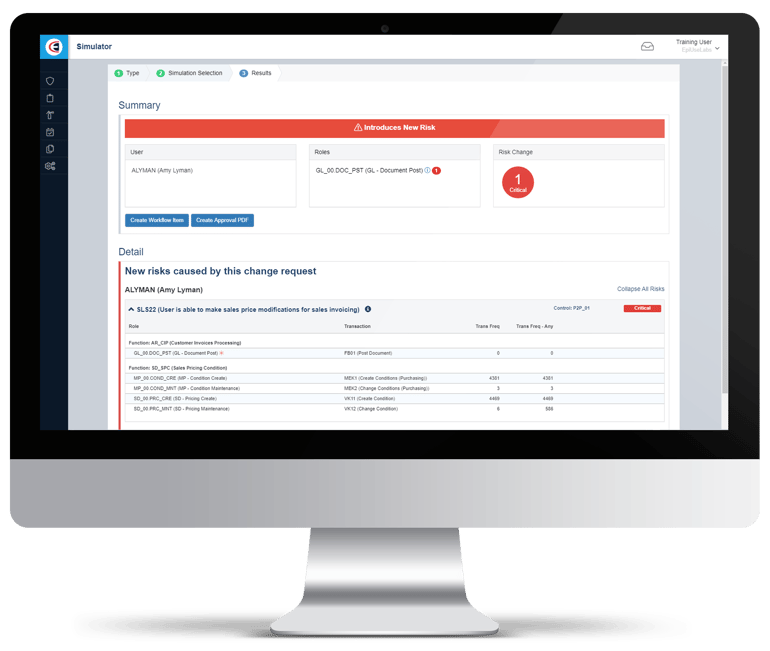
Effective GRC is measured by how well the business users can carry out their Access Risk management activities. And as organisations move to S/4, security is only getting more complex. It is important that organisations implement business-centric GRC to help manage both business and technological changes. These inevitably introduce additional layers of complexity. Get a free SAP risk assessment to start your journey.
Roy is a Professional Services Consultant and Data Security Lead in Europe, focusing on the implementation of Soterion solutions and SAP security consulting. He has 20 years of experience across various industries with expertise in full cycle SAP implementations, SOX certification and compliance, and the design and implementation of SAP Security frameworks, including GRC, Procedures and Technical Models.