Missed the previous articles? Read them here: Article 1 | Article 2
In the third installment of our series on GDPR and POPIA, we will discover a difficult truth. We may love them, but all of our data subjects are high maintenance. Here is what we’ll cover:
- “You are so high-maintenance!”
- It is all about security and quality
- What do the laws say?
- The difference: Removing inaccurate data
- More than a legal concern
- Keep them close, keep them safe
- Want a map? Download this free flowchart poster
- SAP Knowledge Sidebar
“You are so high-maintenance!”
We all know someone like this: they insist on fine-dining experiences, will never go camping for fear of “nature attacks”, expect a gift every week, and will never, ever leave the house without the perfect amount of preening. In the world of relationships, this person might be called high-maintenance. Maintaining data is also a relationship task, and by no means any less effort.
It is all about security and quality
Once acquired, data is stored and maintained for use as production data. Both GDPR and POPIA put emphasis on data security and data quality during the time in which the data is retained.
What do the laws say?
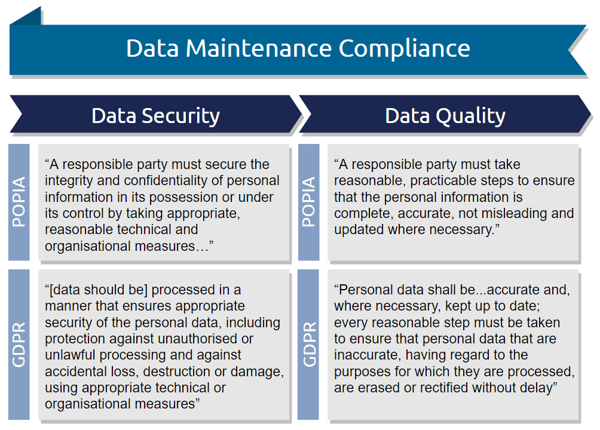
In Article 5, Paragraph 4, the GDPR states: “Personal data shall be...accurate and, where necessary, kept up to date; every reasonable step must be taken to ensure that personal data that are inaccurate, having regard to the purposes for which they are processed, are erased or rectified without delay ('accuracy')."
In Paragraph 6 of the same article the GDPR states: “[data should be] processed in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures ('integrity and confidentiality').”
Among others, in Paragraph 84, GDPR also requires a data privacy impact assessment: “In order to enhance compliance with this Regulation where processing operations are likely to result in a high risk to the rights and freedoms of natural persons, the controller should be responsible for the carrying-out of a data protection impact assessment to evaluate, in particular, the origin, nature, particularity and severity of that risk. “
POPIA addresses the issue of data quality in Section 16 of Principle 5: “A responsible party must take reasonable, practicable steps to ensure that the personal information is complete, accurate, not misleading and updated where necessary.”
Principle 7 of POPIA is called “Security Safeguards” and expands on the topic in Section 19: “A responsible party must secure the integrity and confidentiality of personal information in its possession or under its control by taking appropriate, reasonable technical and organisational measures…”
In Section 19, Subsection 2, POPIA also sets out the need for a data risk assessment; should a responsible party not perform this assessment, they can face fines.
The difference: Removing inaccurate data
POPIA and GDPR are closely aligned when it comes to both data quality and security.
A notable difference is in the way inaccurate data is managed. GDPR is explicit about the removal of inaccurate data (where it can’t be fixed). However, POPIA doesn’t make removal of inaccurate data a requirement.
More than a legal concern
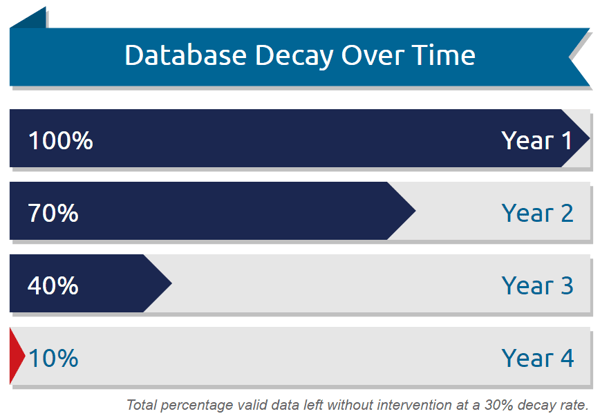
Data quality is largely a policy issue that must be closely monitored and actively solved. Databases can decay at rates of 30% to 70% a year - an alarming fact! Data quality is not only a legal concern, but it is also a key business concern.
Data security, on the other hand, is an extensive topic that has both technical and policy requirements. GDPR and POPIA touch on this in broad strokes, but don’t let that fool you. The devil is in the details, and the details are your responsibility. Privacy auditors are likely to scrutinize security protocols in the event of a breach.
A data risk assessment that takes into account GDPR and/or POPIA requirements is a great way to perform a gap analysis for a compliance strategy. With both data security and quality extending beyond systems and into foundational company policy and procedures, you will need additional capacity to execute the development and implementation of these systems and policies.
Keep them close, keep them safe
Think about the most important person in your life. You want to keep them safe, and you want to keep them close. That is also the secret to maintaining data.
With the amount of personal data we have on our systems, our data subjects are (often unwittingly) in a serious relationship with us. With GDPR and POPIA, the power in these relationships is placed in the hands of the data subjects. This means we have to be far more vigilant and respectful of the data we hold.
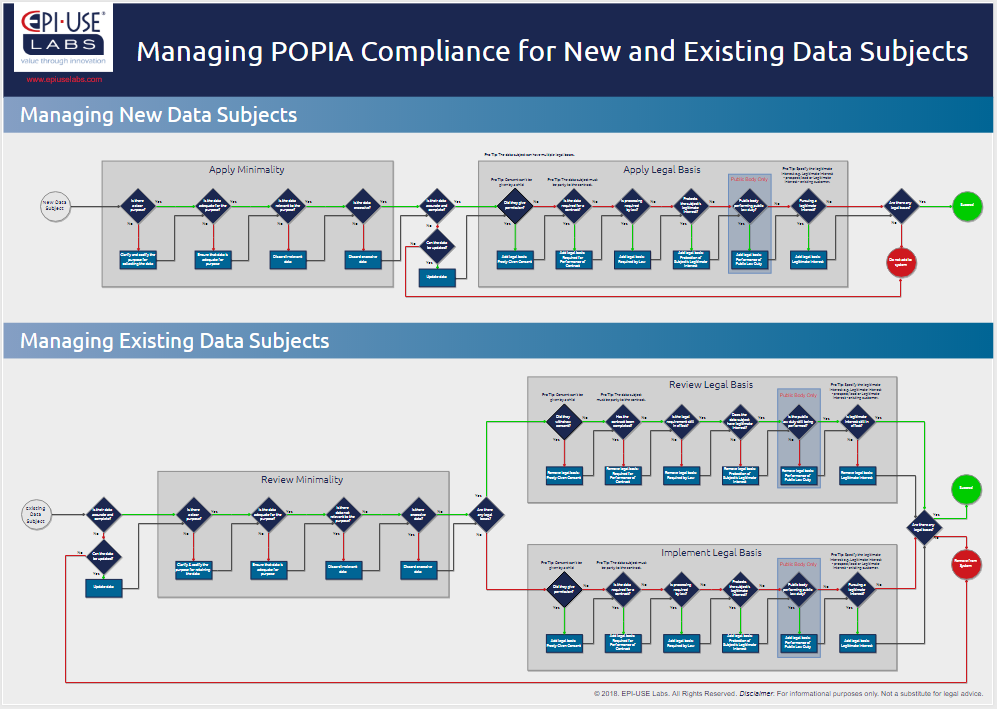
Want a map? Download this free flowchart poster
If it feels like you just can't find your way around data compliance, why not download our free POPIA Compliance flowchart poster? It is designed to help you with data compliance for both new and existing data subjects.
SAP Knowledge Sidebar
Data maintenance and security is where the rubber hits the road for GDPR and POPIA on SAP systems. Data Privacy Impact Assessments are quite broad in scope. One of the key requirements is understanding where data is stored, who has access to it and how it moves between systems. In many cases, SAP acts as a central nervous system that interacts with many other external systems through various interfaces. Understanding this data movement is key to knowing what data you have, how it’s used and where it should be protected. A good way to start is to do a data audit on your business processes. SAP, however, is a complex beast. Data usually exists in multiple places and it’s not always clear where data is stored. For example, customer records may exist in multiple different tables in ERP, CRM and BI systems. In addition, that data may also exist in development, quality and production systems. There’s no single button in SAP that you can push to “Show All” data related to a person. That’s part of the reason we’ve developed Data Disclose, to find data in all the nooks and crannies.
Once you know where the data resides, you should perform a risk assessment to understand what threats and vulnerabilities you need to address to keep the data secure. This can take many forms, but undisputedly securing the systems that store data, or through which the data flows, is important. Doing a security assessment or penetration test might help identify gaps in your armour. Secondly, you should ensure that only people with a need to know have access to this data. This brings us into traditional SAP GRC territory, which many people shy away from, due to its complexity. Fortunately, there are simplified solutions available to identify and correct data access risks, like Soterion’s Access Risk Manager. Instead of a multi-month GRC project, you can nearly instantly audit your access risk specifically as it relates to GDPR and POPIA.
Disclaimer: The information published in the blog post is for informational purposes only and should not be construed as legal advice. Please contact your legal adviser for further guidance on this topic.
Gericke Potgieter
Gericke is responsible for marketing systems management and data analytics at EPI-USE Labs. He is a qualified ISO 27001 Lead Implementer and has an MA in Socio-informatics (Decision Making Theory). He has spent most of his career in IT, strategy consulting and software development.