Do you know the difference between GDPR, POPIA, and dating? We have created a series of nine articles to help you wade through the complexity of at least two of those topics.
In this article, you will learn what the series is about and whether GDPR compliance is equal to POPIA compliance. Let’s get started:
- Data breaches happen, and they are scary
- Managing your privacy throughout the full data lifecycle
- GDPR and POPIA: The highlights
- GDPR and POPIA: Similar, but not the same
Data breaches happen, and they are scary
Data breaches scare people, and rightly so. In South Africa, we have seen massive data breaches in recent years. In a 2017 breach, 60 million identity numbers were stolen which is more than the entire current South African population size. More recently we learned of a data leak of nearly 1 million clients of an insurance company.

Breaches like the ones above happen all too often. Hackers steal names, email addresses, and even medical or credit card data. As consumers, and users of the internet, when our personal data falls into the wrong hands, we become more aware of the data organizations hold about us.
It is more than just breaches that prompt people to ask questions about their personal data. We have all received unwanted emails, phone calls, mobile text messages, and more recently WhatsApp messages, from unscrupulous salespeople. Where did they find our information? And do they even have permission to use it?
Governments around the world are responding to privacy concerns by creating new laws. Through these laws, individuals have more control over their own personal data.
The GDPR legislation created by the European Union is possibly the most well-known example. In South Africa, the POPIA (Protection of Personal Information Act) is a similar piece of legislation. Both laws set out the ways in which personal information can be collected, processed and used by organizations.
EPI-USE Labs has implemented data privacy solutions at a number of leading European businesses. We also implemented processes to become GDPR compliant in our own organization, giving us unique insight into the practical complexities of such privacy laws.
Managing your privacy throughout the full data lifecycle
POPIA and GDPR are strikingly similar in key ways. Beyond the fact that they concern the same topic, POPIA was developed somewhat later than GDPR. This allowed South African legislators to borrow key concepts from the European Union legislation.
Both GDPR and POPIA take the perspective that data privacy extends throughout the entire data lifecycle, from acquisition through to destruction.
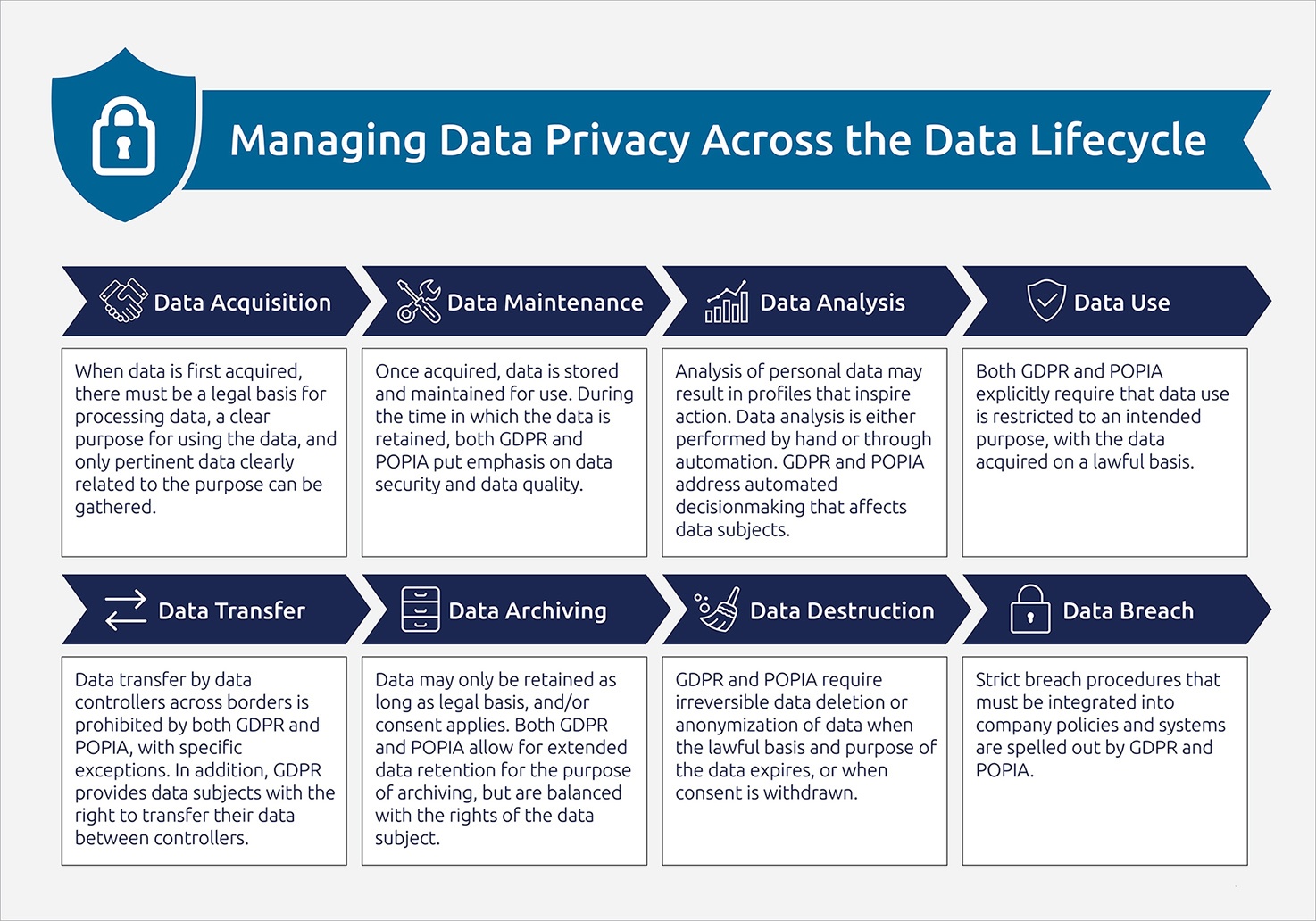
Albeit not exhaustive, this series of articles will compare the two laws in terms of the following topics:
- Acquisition and data entry: When data is first acquired, there must be a legal basis for processing data, a clear purpose for using the data, and only pertinent data clearly related to the purpose can be gathered.
- Data maintenance: Once acquired, data is stored and maintained for use. During the time in which the data is retained, both GDPR and POPIA put emphasis on data security and data quality.
- Data analysis: We use data either directly, or for analysis. Analysis of personal data may result in profiles that inspire action. Data analysis is either performed by hand or through automation. GDPR and POPIA address automated decision-making that affects data subjects.
- Data use: Direct use of data by companies typically consists of contacting people, establishing context, assessing interest or as inputs to analyses. Both GDPR and POPIA explicitly require that data use is restricted to an intended purpose, with the data acquired on a lawful basis. Data subjects must have full access to their data, a simple way to withdraw consent and recourse via a data security officer.
- Data transfer: Data transfer by data controllers across borders is prohibited by both GDPR and POPIA, with specific exceptions. In addition, GDPR provides data subjects with the right to transfer their data between controllers (data portability).
- Data archiving: Data may only be retained as long as legal basis, and/or consent applies. Both GDPR and POPIA allow for data retention beyond these retention periods for the purpose of archiving, but these allowances are balanced with the rights of the data subject to have their data redacted or removed.
- Data destruction: GDPR and POPIA require irreversible data deletion or anonymization of data when the lawful basis and purpose of the data expires, or when consent is withdrawn.
- Data breach: Strict breach procedures that must be integrated into company policies and systems are spelled out by GDPR and POPIA.
GDPR and POPIA: The highlights
POPIA was developed after the initial drafts of GDPR became available. This allowed South African legislators to learn from their European counterparts which led to many similarities. In fact, at face value POPIA may seem like a less verbose version of GDPR, making them interchangeable.
Other than the logical differences in scope (i.e. jurisdiction) and structure, there are a number of key differences that make POPIA challenging. Chief among these is the definition of “person” - where GDPR applies to natural persons as data subjects, POPIA applies to both natural and juristic persons. This adds a significant burden to compliance efforts.
Similarly, POPIA requires an information officer for all organizations to be registered with the Information regulator. With GDPR, not all organizations need a data protection officer.
GDPR and POPIA: Similar, but not the same
With the overlap between POPIA and GDPR, preparation for one will contribute to preparation for the other. However, the significant differences between the two laws mean that compliance to one does not equal compliance to the other.
Join us over the next eight weeks as we delve into the laws, and how they will affect your organization.
SAP knowledge sidebar
From an SAP point of view, there is little distinction between GDPR and POPIA. If you’ve already prepared your systems for GDPR, you only need to revisit the small deltas as outlined in articles in this series. If you haven’t yet started a GDPR project, you shouldn’t get sidetracked by technology. The first step is to ensure you identify all sensitive personal information. You can only manage what you know.
Most likely your SAP systems don’t live on an island and interface with many other systems and providers, like your vendors, banks and client-facing systems. All these should be considered. Our Privacy Comply Methodology outlines the steps of a typical privacy compliance project. Only during the remediation phase do you implement technology that supports your privacy policies and processes.
Disclaimer: The information published in the blog post is for informational purposes only and should not be construed as legal advice. Please contact your legal adviser for further guidance on this topic.
Gericke Potgieter
Gericke is responsible for marketing systems management and data analytics at EPI-USE Labs. He is a qualified ISO 27001 Lead Implementer and has an MA in Socio-informatics (Decision Making Theory). He has spent most of his career in IT, strategy consulting and software development.