Missed the previous articles? Read them here: Article 1 | Article 2 | Article 3 | Article 4
In the fifth blog in our series, we look at the real reason for the existence of GDPR and POPIA: how we use data. This is where it gets really serious. Here is what we'll discuss:
“Will they call?”
If there is one thing that gets the heart racing, it is that first message after the first date. Your phone flickers to life in a way that understates the potential drama to follow. Did they enjoy the date? Will there be a next one? This single message is make-or-break, so you postpone opening it for a few minutes... just in case you seem too eager.
At last, you take a deep breath, tap the message icon and see this:

In utter confusion you are now faced with the choice – you either risk responding via message with “huh?” and make a fool of yourself, or you take the brave step to call them up and ask for some clarification, and perhaps use the opportunity to gauge their ongoing interest.
After scouring their social media profiles for clues, you give up and dial their number. “Hi there, I just stared at your message for the past 30 minutes and I am not sure if what I am seeing is a good thing or a bad thing…”
“Well,” comes the response, “it must be a good thing because I am inviting you for a trip to the zoo.”
Success!
Companies use data to contact customers or gain a deeper understanding of patterns and contexts. For a long time, those very people had no control over how their data is being used. With GDPR and POPIA, the tables are turned, giving the individual (and in POPIA’s context, companies) the power to control their own data.
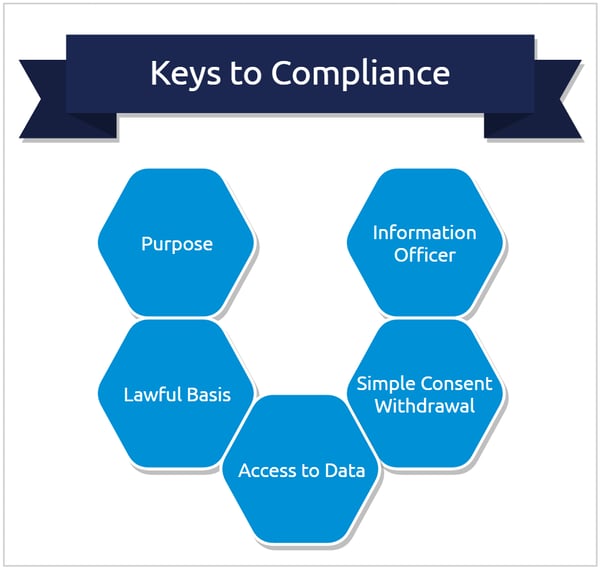
Five keys to compliance
Direct use of data by companies typically consists of contacting people, establishing context, assessing interest or as inputs to analyses. Both GDPR and POPIA explicitly require that data use is restricted to an intended purpose, with the data acquired on a lawful basis. Data subjects must have full access to their data, a simple way to withdraw consent, and recourse via a data security officer/information officer.
How the laws compare
The crux of data privacy laws is that of data use. For that reason, most of the content in both laws is dedicated to it. The table below provides an overview of the applicable sections:
| |
POPIA
|
GDPR
|
|
Data must have a purpose
|
|
- Par. 39 of the Opening Statement
- Art. 5, Par. 1, Sub. 2
|
|
Data requires a lawful basis
|
|
|
|
Data subjects must have access to their data
|
|
|
|
Withdrawal of consent must be simple
|
|
|
|
Organizations may need a data protection officer (GDPR) or Information Officer (POPIA)
|
|
|
You need a data protection officer...
With regards to purpose, lawful basis, data access and withdrawal of consent, the GDPR and POPI Act are essentially identical (albeit that GDPR is more verbose in some regards).
However, where GDPR requires a data protection officer only for specific organizations that process specific types or scales of data, POPIA has no restrictions. Under the POPI Act, all organizations that collect and use personal information must have an information officer that must be registered with the Information Regulator. Where an officer is not formally appointed, POPIA puts the responsibility on the head of the organization.
...and include them early
We’ve discussed some of the policy and technical implications in the article about data acquisition and maintenance. From a policy perspective, there must be clarity of purpose and lawful basis. From a systems perspective, functionality must be put in place that allows for simple data access and withdrawal of consent.
For South African organizations, the appointment of an information officer is a priority, and one not to be taken lightly. Including them from the early stages of developing a compliance strategy is critical to the long-term success of such a project.
No more data hostages
You look at the emojis again. Isn’t a zoo with cows just a farm? What if you are too high-maintenance for cows and other wild animals? What if you realize you don’t like the outdoors nearly as much as your online dating profile stated? How can you easily decline this date without damaging your long-term possibilities?
Before GDPR and POPIA, companies technically held data hostage. People had no way to decline, or object to, the collection and use of their data, or even know what data someone may be holding on them.
How do we stay compliant when using data? It is worth updating the rule of thumb from our article on data acquisition and entry: ask permission, have a valid purpose, let them know what you know, and give them an easy way out.
Need some direction? We have a flowchart for that
POPIA compliance is a challenge. We created this free flowchart poster to help you figure it out. Click below to download your copy.
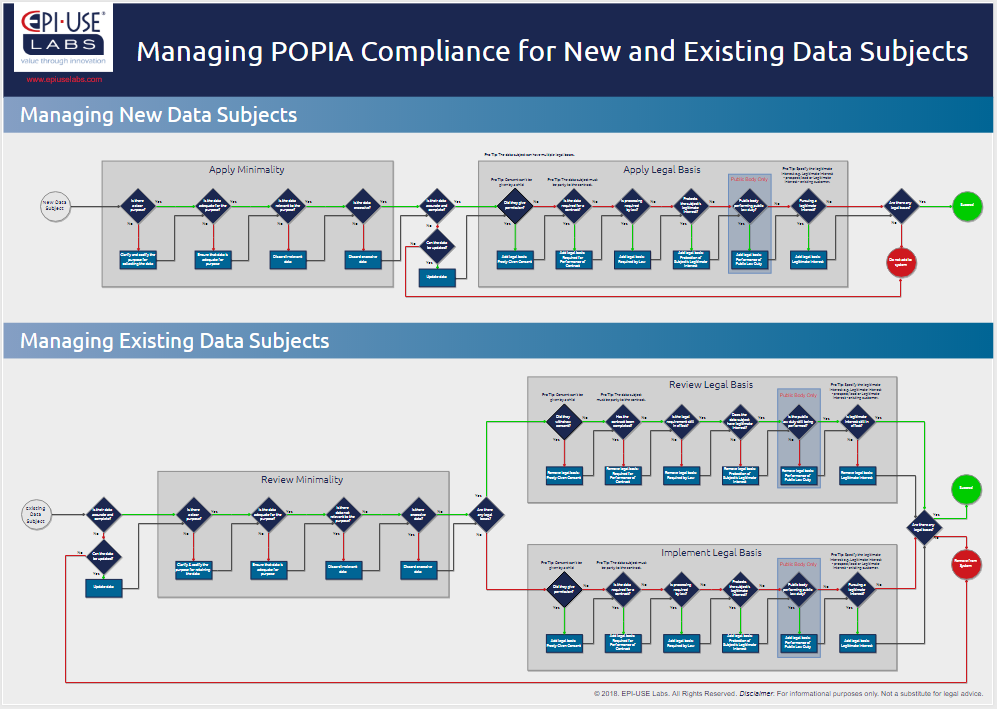
Download your poster today
SAP Knowledge Sidebar
By Jan van Rensburg
One of the easiest ways to lose control of how data is used is to give people access to it. An overeager new hire might not know what the company policy states with regards to data usage. Or a malicious insider could download customer records and sell it to a competitor (something that happened at a previous employer of a close family member of mine). In light of the privacy legislation, it makes sense to review your SAP authorizations and roles, and maybe even do a redesign of everything that can touch sensitive data.
Not everyone needs a major project like SAP GRC to achieve this. EPI-USE Labs recently partnered with Soterion for an easier way to assess access right risks and remediation. Soterion has created rule-sets specifically with privacy legislation in mind. The product makes it very simple to do an initial compliance risk analysis in this space and plan for remediation.
Gericke Potgieter
Gericke is responsible for marketing systems management and data analytics at EPI-USE Labs. He is a qualified ISO 27001 Lead Implementer and has an MA in Socio-informatics (Decision Making Theory). He has spent most of his career in IT, strategy consulting and software development.


